Reporting Private Activities to the Government
Recently, there has been a rise in regulations drafted out of concern for exploitation of children, that have advocated measures that can completely erode privacy on the internet. In 2018 the US Congress passed SESTA / FOSTA, which survived legal challenges by free speech advocates like EFF. This month, the UK again published a draft of the Online Safety Bill which “proposes measures to end anonymous browsing by requiring some online service providers to implement age-verification checks for users.” The State of Utah just passed a bill with similar requirements, ostensibly forcing large online social platforms to begin obtaining proof of age from all their users by 2024.
Many of these regulators don’t understand the implications of what’s possible with technology. Their bills, though vague, can be interpreted so broadly as to end internet use as we know it. And while the initial concern may be for children, subsequent governments can use the snooping apparatus for all kinds of things, as we have already seen the NSA unlawfully do because it was easy. This isn’t restricted to authoritarian countries, but even liberal Western democracies have engaged in covert and illegal surveillance for decades.
The War on End-To-End Encryption
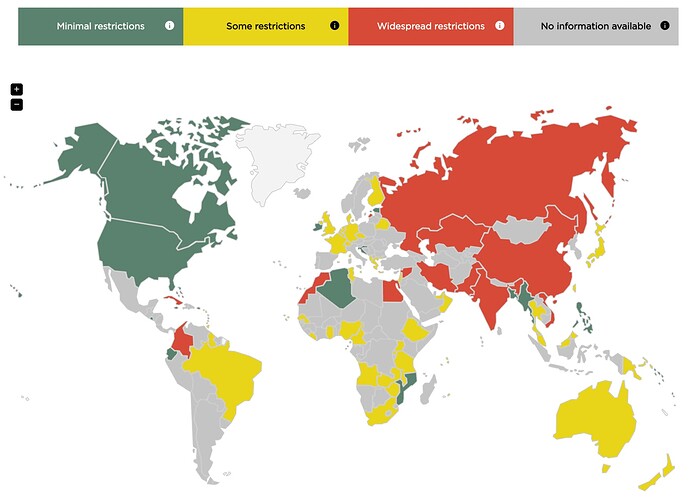
Often, regulators would like to subvert end-to-end encryption: the kind that encrypts conversations all the way between the end-users devices. In the US, the EARN IT Act sought to outright ban this kind of encryption, before an even worse LAED anti-encryption bill was proposed. Trump’s attorney general was vocally in favor after Apple refused to unlock iPhones of a shooting suspect. In Australia, an anti-encryption bill already passed in 2018, and its 2021 “Hacking Bill” can jeopardize privacy and security, with warrantless surveillance. Dubai has banned (ostensibly) end-to-end encrypted messengers like WhatsApp and Skype, except the ones that their government secretly has a backdoor to. Here is the situation around the world:
Source: https://www.gp-digital.org/world-map-of-encryption/
Scanning at the Edge
Advocates of end-to-end encryption say it’s essential and not subject to compromises, but a lot of corporations providing the encrypted messengers have experimented with scanning content on the users’ client software, before it is encrypted and sent from the device. Apple experimented with scanning for Child Sexual Abuse Material (CSAM), but killed the project last year after an outcry. Corporations like Facebook want to read your end-to-end encrypted chats to show you advertising.
These corporations are working together with governments, and advertisers, scanning your conversations whether you know it or not. Much of Big Tech is fueled by ads and have massive incentives to secretly vacuum up your data and even record you without your consent. There is even a name for it: Surveillance Capitalism.
As long as you rely on Big Tech to provide your software, you’ll just have to take their word for it that they don’t have backdoor keys to your encrypted messages, and that they’re not scanning things on the client side. You can do better: with Qbix Platform, you don’t have to trust! People can verify the code does what you expect – or even run it yourself, hosting your own communities with open source software on your choice of computer.
Power to the People
As a company, we’ve spent the last decade building decentralized open source platforms by the people, for the people, which are are independent of Big Government and Big Tech. Empowering any community to choose where to host their social network, even without the internet, goes a long way. It allows communities to get stuff done locally, without permission or rent-seeking behavior from the owners of the infrastructure:
You can see exactly how it works in this video:
Can we balance Privacy and Accountability?
Just because large states and corporations choose the “easy route” of spying on their citizens and users doesn’t mean there aren’t real concerns that communities have about violent crimes and people harming one another. Can a compromise be struck? That is the subject of our feature article: